News of Doctor Web
RSS: Dr Web Security Space
 http://news.drweb.com/rss/get/?c=5&lng=en
http://news.drweb.com/rss/get/?c=5&lng=en
Publisher: Doctor Web
News of Doctor Web
December 24, 2015
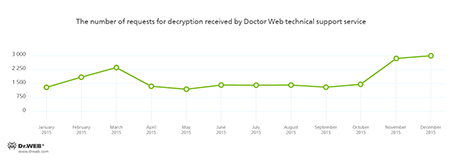
As usual, the first winter month turns out to be rather uneventful in terms of information security, since it is quite rare that virus makers are extremely active on the threshold of New Year and Christmas. This December is not an exception. At the beginning of the month, security researchers detected an installer of unwanted applications for OS X and a Trojan for Linux designed to download and install various programs. Also they have registered a spread of a dangerous banking Trojan for Google Android, which was detected at the beginning of the year and has already compromised more than 31,000 mobile devices.
PRINCIPAL TRENDS IN DECEMBER
- Distribution of new Trojan for Linux
- New installer of unwanted applications that targets OS X
- Distribution of new dangerous banking Trojan for Android
Threat of the month
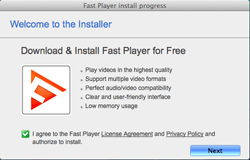
Virus makers become more and more interested in targeting OS X. It is proved by an increase in new malware for this operating system. The majority of threats for Apple computers are designed to deliver advertisements and install unwanted applications. A suchlike malicious program, Adware.Mac.Tuguu.1, was detected by Doctor Web security researchers. This Trojan can covertly install various additional programs (usually useless, but sometimes even malicious) to user’s Mac computer.
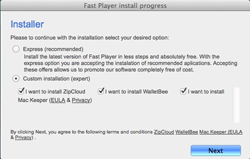
Adware.Mac.Tuguu.1 is distributed under the guise of free programs for OS X. Once launched, this dangerous application reads the content of the ".payload” configuration file located in the same folder as the setup file of the application. Then it detects the address of the command and control server (C&C server), modifies it and refers to the server for the list of additional programs that the user will be prompted to install. All information transmitted between the server and the Trojan is encrypted. Judging from inner numeration used by the installer, there are 736 programs that can be installed on a Mac. Before the installation, Adware.Mac.Tuguu.1 checks if the offered programs are compatible with each other. For example, it will not install the MacKeeper application along with the MacKeeper Grouped application. What is more, Adware.Mac.Tuguu.1 tries to make sure that such software was not installed earlier. Then, before the end of its operation, it checks that the installation was completed successfully. For more information about this Trojan, refer to the review published by Doctor Web.
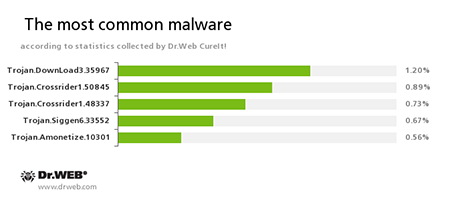
According to statistics collected by Dr.Web CureIt!
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Crossrider1.42770, Trojan.Crossrider1.50845
Trojans designed to display various advertisements.Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.Trojan.Amonetize.10301
A malicious program designed to install other unwanted applications on the computer.
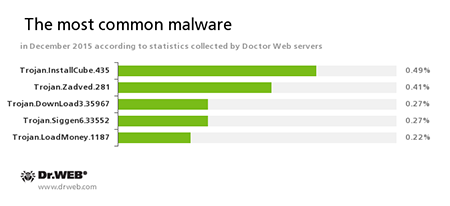
According to Doctor Web statistics servers
Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources.Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
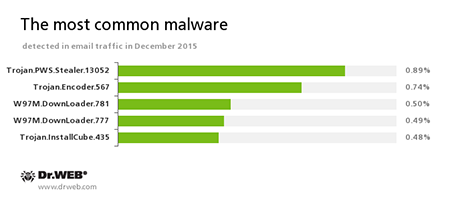
Statistics concerning malicious programs discovered in email traffic
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities of office applications and can download other malicious programs to the compromised computer.Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.
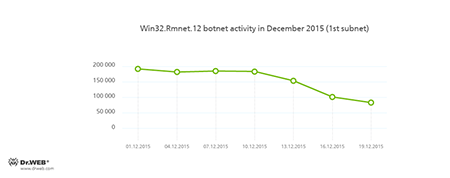
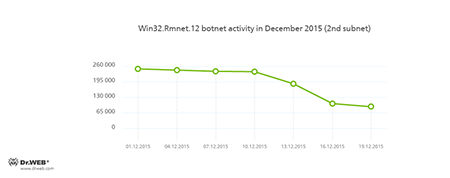
Botnets
Doctor Web security researchers continue to monitor the botnet created by criminals using a dangerous Win32.Rmnet.12 file infector. By the end of the month, a decrease in the both subnets` activity was registered, which is shown in the following graphs:
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
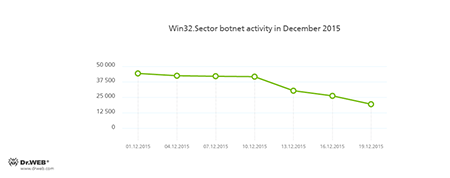
The botnet consisting of computers infected with the Win32.Sector file virus is still active. This malicious program can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
Its average daily activity can be seen in the following picture:
Encryption ransomware
The most common ransomware programs in December 2015
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Linux
The number of malware for Linux keeps growing. Thus, in December 2015, Doctor Web security researchers detected Linux.Rekoobe.1 Trojan that is able to download files from the C&C server and upload them to it upon a command from cybercriminals. The Trojan can also interact with the Linux command interpreter on the compromised device. It should be noted that the first modifications of Linux.Rekoobe.1 were intended to infect Linux devices with the SPARC architecture. However, virus makers have apparently decided to modify the Trojan in order to make it compatible with Intel-based computers. Doctor Web specialists registered the samples of Linux.Rekoobe.1 for 32-bit, as well as for 64-bit Intel-compatible Linux system.
Under specific circumstances, the Trojan establishes the connection to the server via a proxy server. Moreover, to verify encrypted data from the C&C server, Linux.Rekoobe.1 applies a rather complicated procedure. Nevertheless, Linux.Rekoobe.1 can execute only three commands such as: to download or upload files, to send the received commands to the Linux interpreter, and to transmit the output to the remote server—thus, cybercriminals are able to interact with the compromised devise remotely.
For more information regarding this Trojan, refer to the news article published by Doctor Web.
Dangerous websites
During December 2015, 210,987 URLs of non-recommended websites were added to Dr.Web database.
| November 2015 | December 2015 | Dynamics |
|---|---|---|
| +670,545 | +210,987 | -68.53% |
Malicious and unwanted programs for mobile devices
In December, cybercriminals were showing interest in mobile devices—thus, the last month of the year was rather stressful for their owners. Virus makers continued to distribute various banking Trojans that could steal money from users’ bank accounts. Moreover, security researchers have detected a big number of new SMS Trojans. This month, yet another malware program designed to compromise iOS mobile devices was detected.
Among the most noticeable December events related to mobile malware we can mention
- Distribution of dangerous banking Trojans
- Emergence of new SMS Trojans
- Detection of a new Trojan for iOS
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
December 24, 2015
The majority of threats for Apple computers are adware Trojans and installers of unwanted applications. Adware.Mac.Tuguu.1, a malicious program detected by Doctor Web security researchers in December, did not become an exception since it can install different unwanted software on a Mac computer. A Trojan for Linux, Linux.Rekoobe.1, and a banking Trojan, Android.ZBot, were also detected this month. Read about these and other events of December 2015 in the detailed Doctor Web virus activity review.
| Read the full review |
December 15, 2015
Android.ZBot’s first modification was detected this February. Doctor Web security researchers named it Android.ZBot.1.origin. From that time, they have been keeping a close watch on its activity.
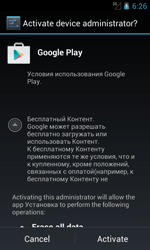
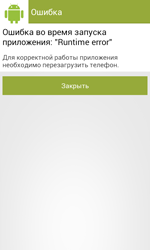
Like many other Trojans for Android, Android.ZBot.1.origin masquerades as a benign program (in this case—as the Google Play application) that can be downloaded once a user visits fraudulent or hacked websites, or other malware can download it to a device. Once the banking Trojan is installed and launched, it prompts the user to grant it administrator privileges. If the privileges are successfully granted, the Trojan displays an error message and urges the user to reboot the system.
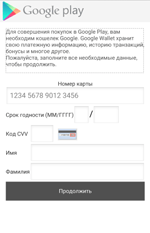
In case the user refuses to grant the necessary privileges, Android.ZBot.1.origin immediately tries to steal the detailed information on their bank card including its number, expiration date, CVV, and the card holder name. To do that, the Trojan displays a bogus dialog simulating the input form of the legitimate Google Play application. It should be noted that the Trojan shows the same dialog even if it gets administrator privileges but only in a period of time after the installation.
Then Android.ZBot.1.origin removes its icon from the home screen in order to “hide away” from the user and starts to control all system events. Thus, the Trojan is launched automatically after the gadget is turned on. Once the malicious program takes over control, it connects to the remote node to get new instructions from cybercriminals and register the compromised gadget on it. Depending on the received command from the server, the banking Trojan performs the following actions:
- Sends an SMS with a specific text to a specified number
- Makes a phone call
- Sends text messages to all user’s contacts
- Intercepts incoming SMS messages
- Tracks the current GPS coordinates
- Displays a special dialog on top of a specified application
For example, once a new compromised device is registered on the server, the Trojan receives the command to check the user’s bank account. If it detects availability of funds, it automatically transfers the specific sum of money to cybercriminals’ bank accounts. Thus, Android.ZBot.1.origin can get access to bank accounts of Android devices users and covertly steal money using special SMS commands specified by online banking services. Moreover, the victim will not have any idea about the theft, since the Trojan intercepts all incoming SMS with transactions verification codes from banks.
It should be noted that some malicious features of Android.ZBot.1.origin (for example, sending text messages) are implemented in a separate Linux library named libandroid-v7-support.so that is stored inside of the Trojan’s program package. It protects the Trojan from anti-virus detection and allows it to stay unnoticed on the device as long as possible.
However, one of the main features of Android.ZBot.1.origin is its ability to steal logins and passwords to access online banking services using fake input forms generated on receiving the server command and designed to create an illusion that they belong to some program. Although this is a classic phishing attack, the way it is carried out in this particular case is rather unique. First, the Trojan receives the instructions that specify an application. Then it periodically begins to check whether the corresponding application is running. The Trojan currently monitors launches of the following applications:
- ru.sberbank.ivom
- ru.sberbank_sbbol
- ru.raiffeisennews
- ru.vtb24.mobilebanking.android
- PSB.Droid
- com.idamob.tinkoff.android
- ru.simpls.brs2.mobbank
- ru.kykyryza
- com.smpbank.android
- ru.ftc.faktura.sovkombank
- hu.eqlsoft.otpdirektru
- ru.ftc.faktura.sovkombank
- uk.co.danwms.fcprem
- ru.sberbankmobile
- ru.alfabank.mobile.android
- ru.alfabank.oavdo.amc
- com.openbank
- ru.ucb.android
- com.idamobile.android.hcb
- com.idamobile.android.ubrr
- com.NGSE.Ubrir
- com.citibank.mobile.ru
- com.ubrir
- ru.rshb.mbank
- com.bssys.android.SCB
- ru.bpc.mobilebank.android
- ua.privatbank.ap24.old
- ru.bspb
- com.svyaznoybank.ui
- ru.avangard
- ru.minbank.android
- ru.letobank.Prometheus
- rusfinance.mb.client.android
- com.artofweb.mkb
- com.compassplus.InternetBankingJava.wscb
- ru.stepup.MDMmobileBank
- ru.abr
- com.intervale.mobilebank.rosbank
- ru.pkb
- ru.stepup.vbank
- ru.vbrr
- com.idamobile.android.Trust
- org.bms.khmb
- ru.tcb.dbo.android
- ru.beeline.card
- ru.rocketbank.r2d2
Once such application is launched, the banking Trojan, using WebView, creates a special web form, the content of which is downloaded from the сommand and сontrol server.
In particular, cybercriminals can specify the size of the displayed dialog, its appearance including a heading and a related text, the number of text fields for data input, images, and etc. The displayed form is “tied” to the attacked application. It means that if the victim of phishing tries to get rid of the shown message and return to the legitimate application dialog by tapping “Back”, Android.ZBot.1.origin will redirect the user to the home screen and close the application. As a result, the owner of the compromised device can assume that this prompt really belongs to the corresponding legitimate application and they should enter the required data. Once the Trojan gets the user’s login and password, it uploads them to the C&C server providing cybercriminals with full control over user accounts in online banking applications.
Virus makers themselves often label these malicious features as web injections, but, in fact, it is not the case—due to restrictions on Android, Trojans cannot inject an external HTML code into dialog forms of the attacked applications.
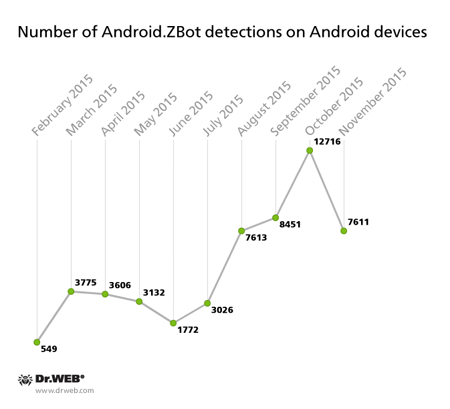
At the moment, Doctor Web security researchers have registered several modifications of Android.ZBot.1.origin that cybercriminals employ mainly against Russian users. Particularly, the first version of this Trojan detected in February is still active: only during last November Dr.Web Anti-virus products for Android detected the banking Trojan on more than 1,100 gadgets. In total, throughout the whole period of observations the Trojan was detected 25,218 times.
Android.ZBot.2.origin—another modification of the malicious program—was detected by Doctor Web security researchers in June. This version has the same features as Android.ZBot.1.origin, but its code is encrypted in order to complicate the detection procedure. In November Android.ZBot.2.origin was found on 6,238 mobile gadgets, and 27,033 cases of Android devices being infected with the malware were registered after the Trojan had been added to Dr.Web virus database.
The following diagram demonstrates the dynamics of Android.ZBot detection on mobile Android devices:
During the examination of the Trojan, Doctor Web security researchers discovered that all its modifications are controlled by virus makers via different servers, the addresses of which are stored in a special database of the malicious program. As a result, devices infected by various modifications of Android.ZBot.1.origin are connected only to their remote nodes creating independent botnets. In total, Doctor Web security researchers have detected more than 20 command and control servers of the Trojan, and at least 15 of them are still active. Our security researchers have managed to get access to three subnets of the Android.ZBot.1.origin botnet. Every botnet consists of dozens and even thousands of compromised devices with their number varying from 140 to 2,300.
The large number of the active Android.ZBot.1.origin.origin’s subnets means that this Trojan is a commercial product and is distributed through underground hacker markets where it can be purchased by a single cybercriminal or by organized group of virus makers. It is also proved by the fact that the administration panel for the botnets that were created based on the devices infected by Android.ZBot.1.origin has a limited license and is used as a subscription service. We cannot exclude the possibility that fraudsters will not limit their targets to Russian users only, and not expand the geography of these attacks to other countries including Europe and the United States.
Doctor Web recommends owners of Android devices that you download applications only from trusted sources and do not install suspicious programs. Dr.Web Anti-virus successfully detects all the known modifications of Android.ZBot.1.origin for Android, so they do not pose any threat to our users.
December 15, 2015
In particular, it resolves an error 1011 issue that could occur during activation of a serial number if Dr.Web CureIt! was launched prior to another Dr.Web anti-virus.
| Download Dr.Web CureIt! |
December 15, 2015
In particular, it eliminates a defect that caused component's abnormal termination if the prompt mode was enabled for system services in security settings.
The update will be downloaded and installed automatically.
December 14, 2015
Both applications have received revamped and optimised routines for detecting and neutralising malware as well as other tweaks and bug fixes.
Dr.Web Security Space for Android can now detect Stagefright 2.0 vulnerabilities. Also resolved was a virus database updating issue that could occur when the application communicated with a centralised protection server in mobile mode. The update upgrades the routines for interacting with Android TV.
The updated applications are available at Google Play (Dr.Web Security Space , Dr.Web Security Space Life, and Dr.Web Anti-virusLight) as well as on Doctor Web's site.
If you downloaded your Dr.Web application from Google Play, the update will be downloaded and installed automatically. If you’ve disabled automatic updating on your device, go to Google Play, select Dr.Web Security Space, Dr.Web Security Space Life or Dr.Web Anti-virus Light on the application list, and click "Update”.
To update via the Doctor Web site, you need to download a new distribution file. If you enable the settings option “New application version”, a new version notification will be displayed whenever the virus databases have been updated. You can start the download directly from this dialogue box.
December 10, 2015
A Control Service issue that resulted in its abnormal termination when interacting with the data loss prevention routines has been resolved.
Also eliminated were Dr.Web Net filtering service defects resulting in application installations and updates carried out via the Windows Store being blocked whenever encrypted traffic was scanned. And the problem causing the CPU load to increase when encrypted connections were being filtered has also been resolved.
A self-protection module error that could result in applications terminating abnormally while the component was running has been corrected.
The update will be performed automatically; however, a system reboot will be required.
December 10, 2015
The cause of a critical system error occurring when 32-bit editions of Windows interacted with the module has been resolved.
The update will be performed automatically; however, a system reboot will be required.
December 10, 2015
An agent registration error that occurred if a proxy server was being used to connect to the Internet has been corrected.
A Dr.Web SelfPROtect defect that made Dr.Web Preventive Protection block the launch of Mozilla Firefox if the Secure Browser option was enabled in ESET NOD32 Smart Security 9.0 has been resolved.
The update will be performed automatically; however, a system reboot will be required.
December 9, 2015
Like other modifications of this malware, Adware.Mac.Tuguu.1 can covertly install various additional programs (usually useless, but sometimes even malicious) to user’s Mac computer. The commercial interest of cybercriminals is to get money for every successful installation of such applications.
Adware.Mac.Tuguu.1 is distributed under the guise of free programs for OS X. Once launched, this dangerous application reads the content of the ".payload” configuration file located in the same folder as the setup file of the application. Then it detects the address of the command and control server (C&C server) and modifies it. Using an encrypted request, Adware.Mac.Tuguu.1 refers to the C&C server for the list of additional programs that the user will be prompted to install. The server response is also encrypted and contains several fields that determine what applications should be installed to the user’s Mac. Judging from inner numeration used by the installer, there are 736 programs. Every program has its own conditional “rate” for Adware.Mac.Tuguu.1. It means that due to the limited maximum number of applications that can be installed at a time, the installer, using specific algorithm, tries to create an optimal list of compatible software with the highest “rate”.
Before the installation, Adware.Mac.Tuguu.1 checks if the offered programs are compatible with each other. For example, it will not install the MacKeeper application along with the MacKeeper Grouped application. What is more, Adware.Mac.Tuguu.1 tries to make sure that such software was not installed earlier. Then, before the end of its operation, it checks that the installation was completed successfully.
The dialog of Adware.Mac.Tuguu.1 has the Custom Installation mode, which shows check boxes that allow to refuse all the additional software. That is why, this malicious program cannot be labeled as a Trojan. However, Adware.Mac.Tuguu.1 is a typical adware that is quite able to “litter” the operation system with useless software taking advantage of the user’s carelessness. Dr.Web Anti-virus for OS X can detect and remove this program, so it does not pose any threat to Dr.Web users.